ISO27005 for information systems risk management (ANSSI text)
ISO recently published the revision of ISO/IEC 27005:2022. The ISO/IEC 27005 standard, applicable to all types of organizations, is an international standard containing guidelines relating to information security risk management. It is designed to help implement information security based on a risk management approach. The ISO/IEC 27005:2022 revision makes it possible to provide and disseminate the main innovations of EBIOS Risk Manager through the standard. The task force of French experts organized by AFNOR (Structure AFNOR/CN CYBERSECURITE | Norm'Info) in conjunction with the EBIOS Club and ANSSI (represented by the Cyber Risk Management office) participated for more than three years the work to revise the ISO/IEC 27005 standard.
Who is the ISO 27005 standard for?
The International Organization for Standardization recommends the ISO 27005 standard to companies, but also to public establishments such as “governmental agencies” or NPOs, non-profit organizations.
Concretely, this information security standard is mobilized to ensure the confidentiality of data, but also the accessibility and integrity of strategic information for the organization. It is deployed within all structures concerned by cyber risks and the continued growth of data in their services.
What exactly is the ISO/IEC 27005 standard for?
Behind the standard is training, which allows employees to develop the skills to implement effective IT risk management. People trained in ISO 27005 are theoretically able to identify cyber risk, analyze it, measure it and treat it.
The objective of this standard also consists of installing an ISMS, an Information Security Management System. The ISMS includes the definition of cybersecurity processes and policies, coupled with a continuous improvement approach to risk management. It is supposed to take into account human and technical factors.
With this in mind, the ISO 27005 standard is deployed around a logic comparable to that of continuous improvement PDCA (Plan, Do, Check, Act):
- Plan: Identification and assessment of cyber risks, then strategic reflection on risk reduction actions;
- Do: Implementation of these actions;
- Check: Control of results;
- Act: Monitoring and improvement of the risk treatment strategy.
What are the ISO 27005 training courses?
There are several certification courses available to train in ISO 27005:
- ISO 27005 Foundation, which gives access to the PECB Certified ISO/CEI 27005 Foundation certification;
- ISO 27005 Certified Risk Manager with EBIOS: this training considers risk management through the prism of the EBIOS method. It therefore gives access to two exams: PECB Certified ISO/CEI 27005 Risk Manager and PECB Certified EBIOS;
- ISO 27005 Certified Risk Manager with MEHARI, “harmonized risk analysis method”, developed by CLUSIF in France;
- ISO 27005 Risk Manager from ANSSI, the National Information Systems Security Agency.
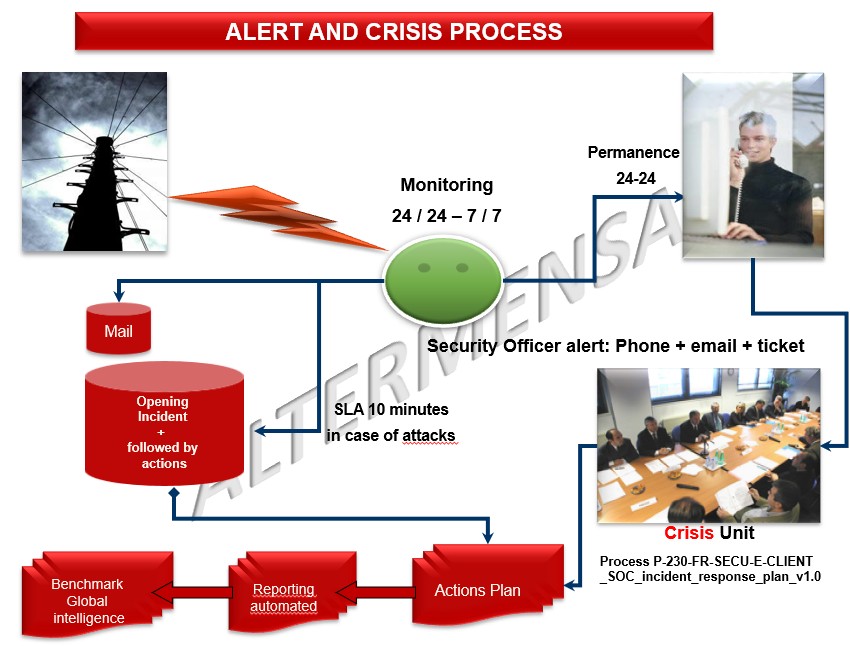
Risk Management (ISO 27005)
Standard 27005 presents an approach
Establishing the context for the risk analysis
Definition of SSI risk assessment
Choice for SSI risk treatment
Acceptance of risk
Communication and consultation relating to SSI risks
Monitoring and review of SSI risk.
Limits:
The organization must define its own approach
Methods often requiring training and not adaptable to all situations
Dependence on IS mapping: depth, extent, etc.
Tendency towards completeness
Accumulation of technical measures without overall coherence
Benefits
Defines a rational approach that has resulted in methods that work
Great flexibility: used in all circumstances, especially during changes
Pragmatic and usable on its own, it can also be suitable for small organizations.